•This cycle tells the beginning to end phases of an Red Team engagement in an organization.
Extensive OSINT
• This phase generally deals with gathering more and more information about the target organization.
• Social media sites, platforms where employees are generally active are of primary focus.
• Attackers with access to tons of information available in the internet tries to find out the sensitive ones which can be used for further exploitation purposes.
Initial Access & Execution
• Initial Access consists of using various entry vectors to gain access within the internal network.
• There are ways like exploitation to External Remote Services, mis-configurations in Web Applications etc. which may lead as gateway to the internal network.
• There are a lot of ways to get initial access, however it depends on the technologies used by the organization which could be identified in the previous section.
• Execution is attacker-controlled code running on the target machine. For example: An adversary might use a remote access tool to run command prompt that does network discovery.
Persistence & Privilege Escalation
• Attackers always look for hidden techniques to keep access to systems across restarts, changed credentials etc which could cut-off attacker access.
• Examples: Resetting password of a low-profile user & using it as a backdoor to network.
• Privilege escalation is gaining higher-level permissions on a system or network. Common approaches are to take advantage of system weaknesses, misconfigurations, and vulnerabilities
• Elevated Access Accounts: -
• SYSTEM/root level
• Local Administrator
• User with admin-like capabilities
• Privileged Groups etc.
Lateral Movement
• Lateral movement is when an attacker compromises or gains control of one asset within a network and then moves on from that device to others within the same network.
• Attackers might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier.
• Example:
• Internal Phishing: Attackers may use internal phishing to gain access to additional information or exploit other users within the same organization after they already have access to accounts or systems within the environment.
• Remote Services: Threat Attackers may used valid credentials to log into services like SSH, VNC, RDP
and then perform operations etc.
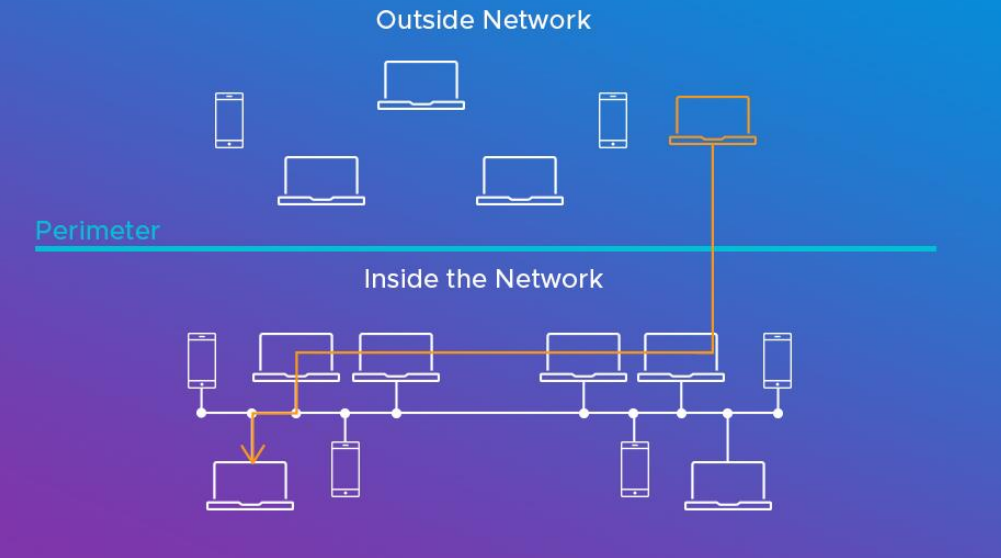
Defensive Evasion
• Defensive Evasion deals with avoiding detection throughout the compromise.
• Attackers bypass detection by obfuscating malicious scripts, hiding in trusted processes, and disabling security software etc.
• Defensive evasion benefits from discovery but is more related to understanding how an attacker can avoid network defenders, whether through certain processes or knowing which security tools are on a system.
• Example:
• Impair Defenses: This includes disabling Firewalls and anti-virus and detection capabilities that defenders can use to audit activity and identify malicious behaviour.
Discovery
• Attacker head for situational awareness where they try to figure out organization environment
• These techniques help adversaries observe the environment and orient themselves before deciding how to act.• This helps a lot in gathering the whereabouts and critical assets located in the network architecture.
• Examples:
• File and Directory Discovery : Attackers enumerate files and directories or may search in specific locations of a host or network share for certain information
within a file system.
Data Collection
• Data collection is the process of gathering and measuring information from established system.
• The data collected can be any sensitive information present in a system/network.
• Example:
• Archive Collected Data: An adversary may compress and/or encrypt data that is collected prior to exfiltration
• Clipboard Data: Attackers may collect data stored in the clipboard from users copying information within or between applications.
Data Exfiltration
• Once all the critical data has been identified and packed, attackers will try to steal data from the computer/network.
• Attackers can also compress and encrypt the collected data.
• Examples:
• Automated Exfiltration: Attackers may exfiltrate data, such as sensitive documents, through the use of automated processing after being gathered during Collection.
• Exfiltration over Physical Medium: Attackers may attempt to exfiltrate data via a physical medium, such as a removable drive.
Red Team Infrastructure
• C2 Server : These are used by attackers to maintain communications with compromised systems within a target network.
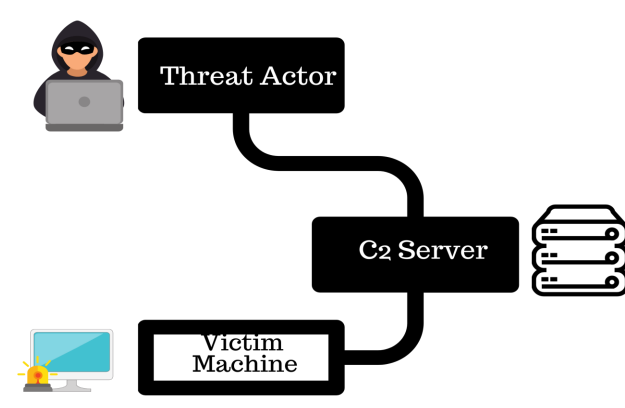
• Payload-Server : This is a dedicated server hosting all the malicious scripts, executable etc and this is accessible from both attacker and victim network.
• Redirector Server : A redirector is a system that proxies all traffic to your command and control server.
• Threat actors doesn’t use one system to launch attacks and get shells. They setup multiple systems to act as pivot points (redirectors) back to their C2 Server.
• These prevent the client from being able to see our actual C2, and should be easy to
spin up and tear down.
• It sits between victim environment and attacker network, listens for connection from the target machine and forward it back to the attacker.
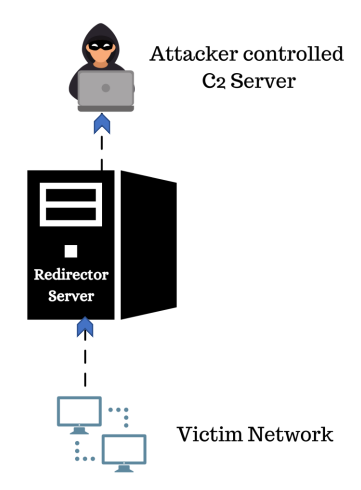
• It protects the original location of the team server.
• Adversary Emulation is mimicking of someone or something else. Based on threat intelligence, you determine FIN10 group is most likely to target an organization.
• Example: To emulate this adversary, you mimic the TTPs they use and test those in your environment. You behave exactly like they would.
• Adversary Simulation, you want to make it look like a real attack is happening while there is no real adversary.
• You make use of TTPs that work in the environment at hand, irrespective of which APT actually uses them
• Advance Persistent Threat [APT] : An advanced persistent threat is a stealthy threat actor, typically a nation state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period.
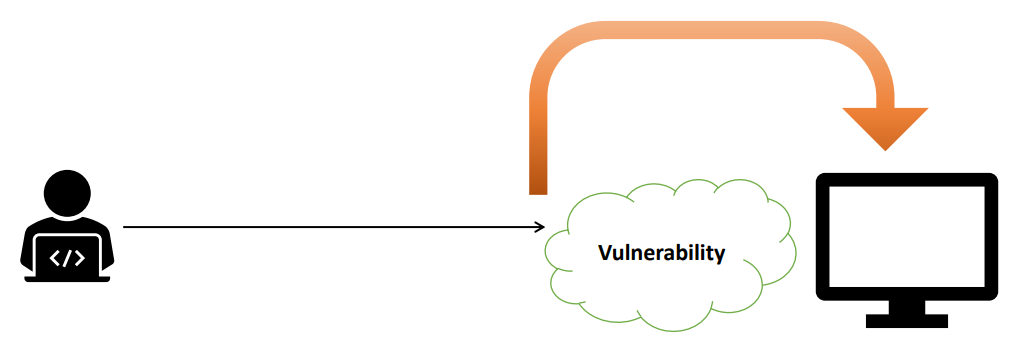
• Exploit : It is the actual code through which can attacker take advantage of a particular loop-hole.
• Vulnerability: -
• The loop-hole existing in a particular software or hardware can be called as vulnerability.
• It can also be understood as a weakest link which allows an attacker to compromise the system.
• De-Militarized Zone Network (DMZ Network) :
• It is a network (physical or logical) used to connect hosts that provide an interface to an untrusted external network
• The systems that are most vulnerable to attack are those that provide services to users outside of the local area network, such as e-mail, Web and Domain Name System (DNS) servers are present inside a DMZ
• The ultimate goal of a DMZ is to allow access to resources from untrusted networks while keeping the private network secured.
• Militarized Zone Network (MZ Network) :
• Zone having maximum security and is one of the most secure segment in the environment.
• Contains critical information about the organization etc.
• All operations in the organization is managed from Militarized network.
• Tactics, Techniques and Procedures (TTPs)
• TTPs explains how threat actors orchestrate and manage cyber-attacks.
• It explains the methods associated with a specific threat actor or a group of threat actors.
• A “Tactic” is the highest-level description of threat actor behaviour.
• ”Techniques” give a more detailed description of behaviour in the context of a tactic
• “Procedures” an even lower-level, highly detailed description in the context of a technique
• Listener: -
• Listener waits for an incoming connection from the target machine.
• In our lab scenario, we will listen on our Kali machine and the target machine can connect back to our machine after successful exploitation.
• Basically listening means opening a port and waiting for connection from the target machine.
• Tools like netcat is one of the best example available for both windows and linuxplatforms.
• Exploitation : -
• Exploitation is a phase to be performed after proper identification of a vulnerability.
• A Service running on a system, a Web Application, software are the primary target for exploitation.
• Improper identification of the vulnerability with various incompatibility issues may crash the vulnerable/target service or software.
• Hence the target must be intensely enumerated before entering in this phase.
• Basically, in this phase the attacker enters the target system after taking advantage of the existing vulnerability in the product.
• The access can be physical or remote, but we will demonstrate in a remote situation.
• If the exploit succeeds, the actual code of the payload runs.
• Scenario specific example :-
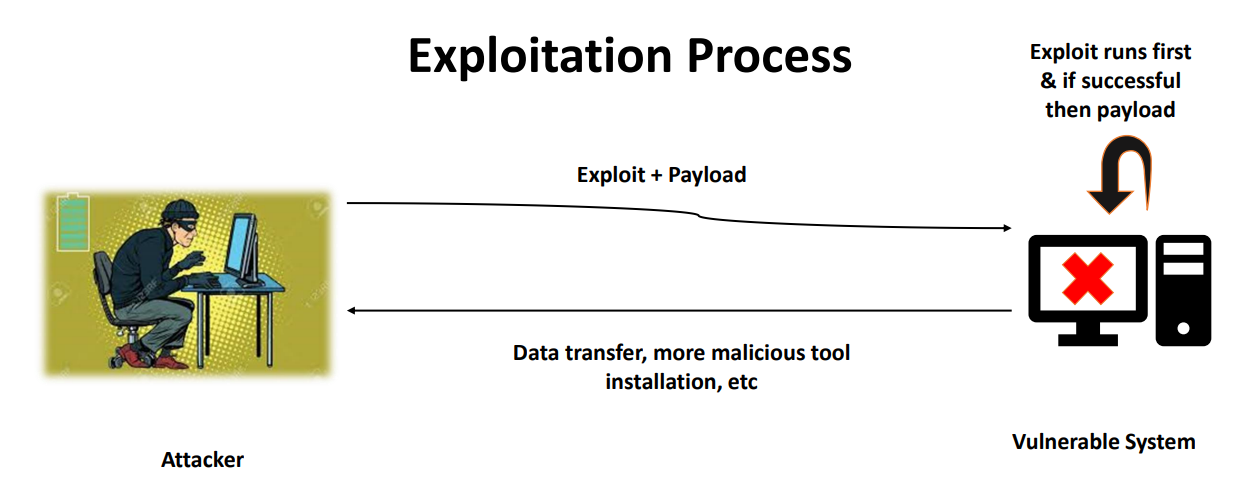
• Singles
− These are self-contained payload assigned to do a specific task that is, create a user, or a bind shell.
− Example: payload/windows/adduse
• Stagers
− These type are payload are used to download large payload to the target machine from the attacker machine.
− Creates a network connection between attacker & compromised machine.
− Example: payload/windows/shell/bind_tcp
• Stages
− These are the large payload downloaded by the stagers & then executed.
− Assigned to do complex tasks like Remote Desktop, meterpreter etc.
− Example: payload/windows/shell/bind_tcp
• Shells are non-GUI interaction with the system, one can interact & manage the environment of the system through shell.
• It is used for administration purposes & at times described fruitful compared to GUI.
• Examples:
• In Windows:
• Command Prompt
• Power Shell
• In Linux:
• Bash shell
• sh shell
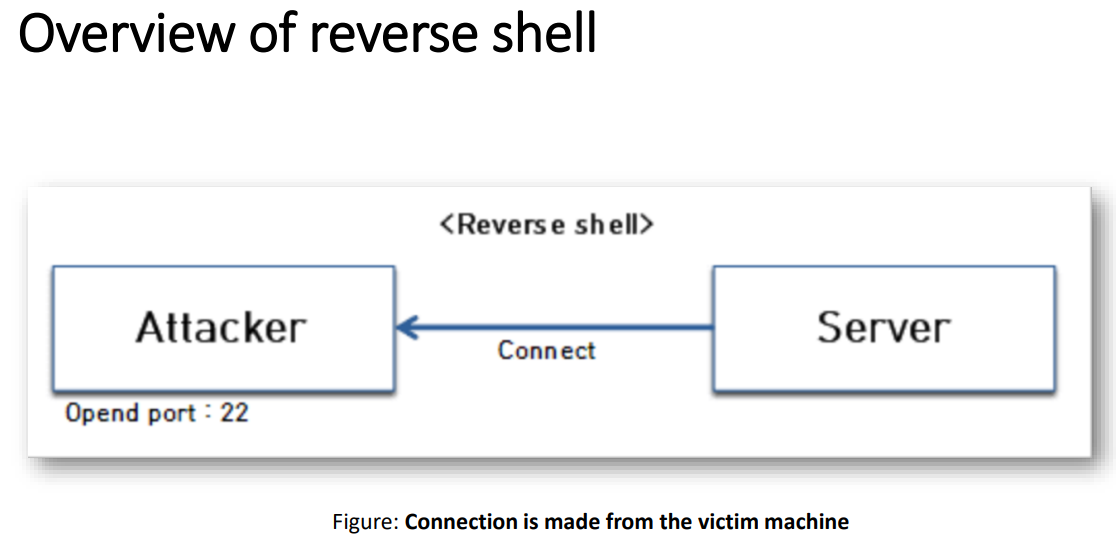
Reverse Shells
• Here, the target machine connects back to the attacker box.
• All communication goes through specific TCP ports.
• We need to have listener active on the attacker machine.
• We will take example of the swiss army knife tool (aka netcat).
Bind Shells
• Here the attacker machine connects to the victim system.
• The attacker opens a TCP port on the victim machine & host a shell.
• That means anyone who connect to the target machine & on a specific port will be presented with a shell.
• The shell can then be used to spread the compromise.